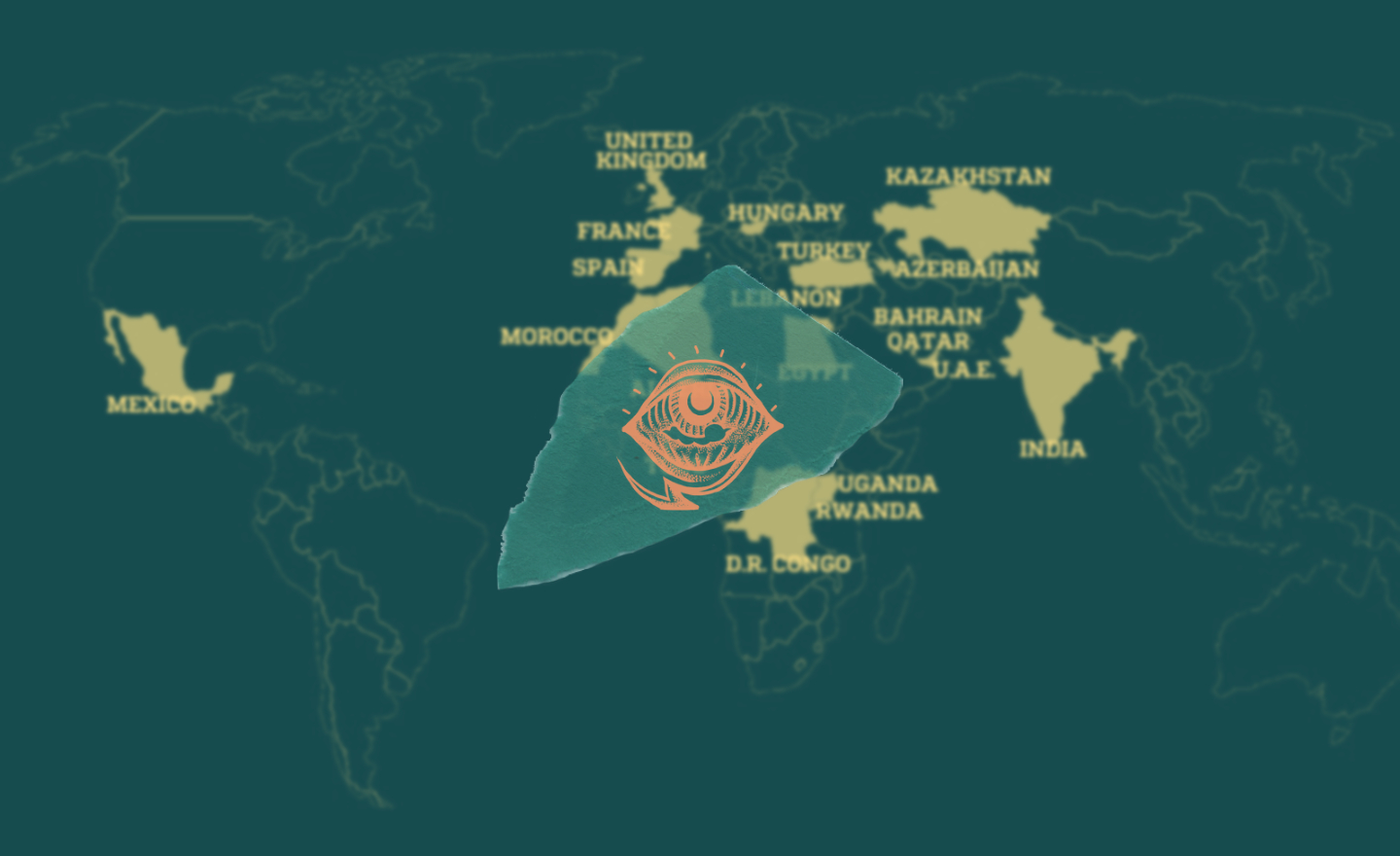
A recent security leak revealed that Israeli NSO Group’s malware has targeted around 50,000 devices worldwide, including those of journalists and activists in a number of Arabic-speaking countries. Forbidden Stories, supported by Amnesty International Security Lab, released a collaborative investigation into the leaks, led by 80 journalists from 17 international media organizations, including Lebanon’s Daraj.
While this is not the first time Pegasus targets activists and journalists, this recent investigation revealed the magnitude and ease at which governments spy on their citizens in countries such as Saudi Arabia, Bahrain, Morocco and UAE.
This leak in NSO Group is extremely important for two reasons: First, Pegasus is a sophisticated mobile malware that allows governments to intercept phone calls and text messages. Second, the leak was by Israelis and was uncovered by international researchers.
NSO uses 0-day exploits, a type of security vulnerability that allows threat actors to gain remote access to target devices (phones, laptops, servers etc.) and extract confidential data. NSO’s business model is mainly geared towards selling spyware to governments and intelligence agencies willing to target political opponents.
The surveillance company is historically known for using undisclosed and not-public 0-day exploits, which makes protection against such a threat tricky and complex. Usually, these exploits are immediately patched by software vendors after being detected or disclosed publicly.
Secure Your Devices!
NSO’s zero-click attacks are almost undefendable. However, we always recommend implementing the basic security measures:
- Regularly update your endpoint devices and infrastructure while applying vulnerability patches and the latest security updates released on Android, iOS, and Windows. This will reduce the risk of exposure to known vulnerabilities and exploits. Servers used and controlled by organizations and individuals, including network infrastructure such as routers and communication dongles, should be patched and regularly updated as well. Using an obsolete system or an old version of an OS exposes you to a higher risk of a targeted attack.
- Enable firewalls on your main work devices: firewalls are usually available on your devices by default, and they should be enabled to protect your network and your traffic from potential threats.
- Avoid sharing your account’s authentication information with other users if they don’t need it. Try sharing the information directly instead of giving access to your own account. Review access privileges on your devices, router, servers etc. All permissions that are not needed by other users should be disabled.
- Install strong antivirus (like Avast and AVG) and anti-malware software (like MalwareBytes) on your devices and servers: Investing in an antivirus protects your devices from malicious applications and provides constant updates of malware heuristics.
- Use the latest available version of a web browser on your phone and laptop.
- Use password managers to generate complex passwords and avoid redundancy.
- Develop awareness on phishing attacks and digital hygiene: Raising awareness and conducting training in your organization helps in detecting phishing attacks, a type of social engineering attack used to steal your data or to install malware on your device. Phishing attacks abuse human misperception and inattention to succeed. Checking the URL and emails before opening a link is a good practice.
- Do not click on a link from unknown or suspicious sources.
- Limit the number of softwares on your device; the less the better. Avoid installing unnecessary software on your device.
- Separate personal and professional devices: Using two devices to separate your personal content from your professional content. It’s part of the physical segregation of data so in case of a breach, the impact will be reduced.
- Report in case of doubt: In case you got a link from suspicious sources, or if its content seems strange, contact cybersecurity experts for further information and investigation. You can reach out to SMEX, CitizenLab and Amnesty.
Feature image: Original map via Forbidden Stories: Countries where journalists were selected as targets.
Source: SMEX